Before proposing an answer to this question, which has been circulating in the cybersecurity world of late, we need to have an idea of where this question comes from, and what SIEM and SOAR can offer the SOC and the Threat and Vulnerability Management department.
SIEM, the SOC window
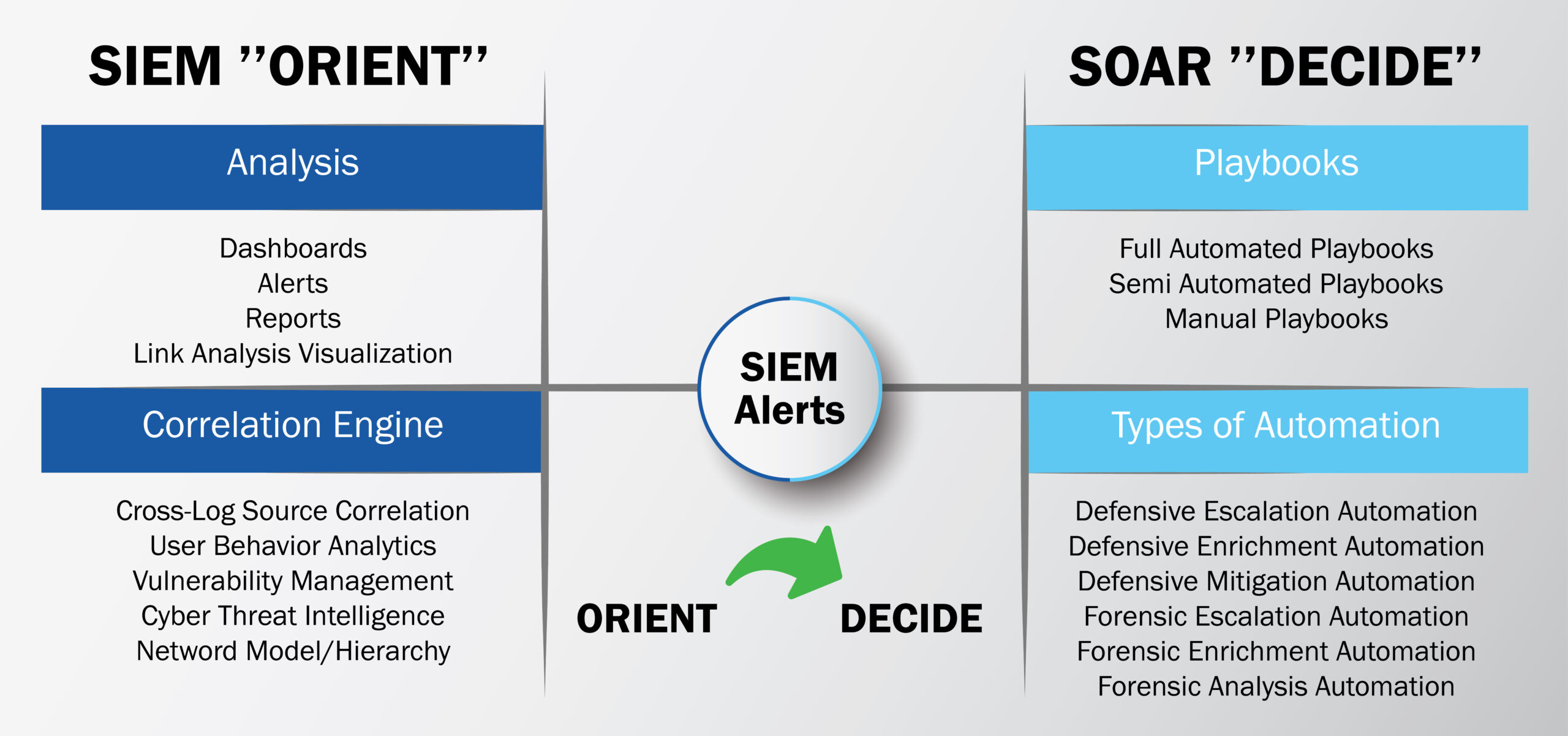
SIEM, or Security Information and Event Management, is an essential tool in every security center. This tool enables security teams to read, understand and interpret the countless logs received by all IS equipment, including firewall logs, workstations and applications.

SIEM also enables the creation of scenarios and alerts based on the correlation of data received from the company’s various devices.
To explain a little more about what a SIEM can offer, we’ll look at a use-case that can be found in any company.
Let’s assume that a malicious e-mail has found its way to the inbox of a user who, unfortunately, has clicked on the link or attachment contained in the e-mail, triggering a whole process of workstation and network contamination.
By collecting logs from mailing servers, network nodes, workstations and Active Directory, we can see that the attacker tries to contact an external server (workstation log) after downloading, the malware tries to create a user account on Active Directory (AD log) using this account and the victim’s account, the user tries to gain access to other workstations using known vulnerabilities (workstation log).
Using all these logs and all this information, the SIEM will create a sort of attack path or chain, tracking traces, dates and actions; the security teams in the SOC will quickly and easily know the first point of entry and the impacted services, so they can remediate and stop the infection and the attack in progress.
However, despite all its successes, the SIEM has several weaknesses, including the difficulty and complexity of the scalability aspect, as well as the number of false positives that require enormous processing time, given that the logs never stop and that detection in a SOC takes place 24 hours a day, 7 days a week and 365 days a year. But it also requires a highly-trained team to manage it all.
SOAR, a major time-saving asset for the SOC
As a set of software and tools, SOAR (Security Orchestration, Automation and Response) not only detects and takes action on low-level incidents, but also adds layers of vulnerability and threat management. It also orchestrates and automates these tasks to save time. For example, in addition to alerting CSIRT, SOAR will automatically add blocking rules to the firewall, create incident tickets and send them to the relevant teams.
Taking the SOC example again, SOAR will even disconnect the workstation that opened the attachment, temporarily block the AD account created by the attacker, and send alerts to all parties concerned. With the right configuration and adaptation, SOAR will minimize damage and save precious time for SOC engineers.
This explains why many security experts believe that SOAR answers the questions that SIEM leaves unanswered.
And why not complement each other?
In the most advanced SOCs, SOAR and SIEM work in perfect harmony, although many believe that SOAR replaces SIEM entirely.
Even so, we’re finding that SIEMs are improving over time, adding next-gen features to help security experts better manage cybersecurity challenges.
After several comparisons, we believe that the SIEM will not be replaced by the SOAR, but on the contrary, like any good product, the SIEM will be open to cooperation with SOARs to create a complete solution ready to face the challenges of the future. The mix between the two can increase SOC efficiency.

