Phishing is the most common malicious practice used by cybercriminals on the Internet. You, the reader of this article, have probably received dozens or even hundreds of fraudulent phishing messages through your private or professional e-mail inboxes, via SMS or by fraudulent phone calls pretending to be a trusted third party.
In this blog article, we give you some keys to identifying these phishings, so you don’t fall into the traps set by increasingly structured criminal organizations.
1. Never communicate sensitive information by e-mail or telephone.
You’ll probably have read about it in information messages from your bank, delivery company or social security (Ameli.fr), since all these organizations and many others, both private and public, are blocking web threats.
Any trusted organization will warn you with a message similar to the following: “Our organization never asks you to communicate your personal data by telephone or e-mail”.
This information is vital to your protection, and is regularly repeated to you, so that you never divulge personal, sensitive or banking information in the face of these fraudulent schemes. What we call “psychological hacking” is more widely known in the world of IT and cybersecurity as social engineering.
2. Check the sender’s e-mail address
When you receive an e-mail, you only see the “sender’s name”, not the full e-mail address. In reality, you only see what they want you to see.
So let’s take a look at how to identify the real sender of an e-mail in a real-life phishing case.
This phishing scam impersonates SHEIN.fr, a highly successful and trendy fast-fashion company, and is therefore being exploited by cybercriminals.
You receive an e-mail from SHEIN.fr and open it.
Having doubts about the structure of the e-mail, and because the offer is too good to be true, you decide to check the sender’s address.
Simply click on the sender’s name, and you’ll find out whether his or her shipping address appears to be correct and legitimate.
If the address doesn’t match, block it immediately.
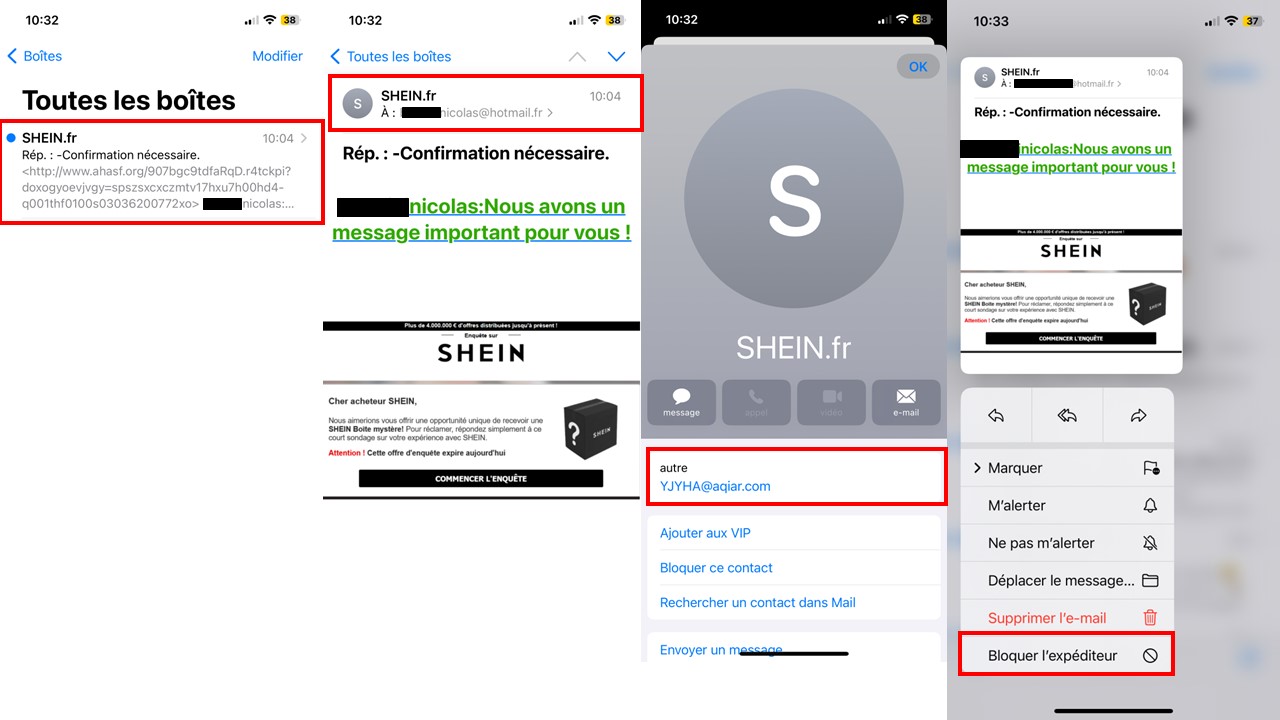
Beware: hackers know how to use e-mail addresses with a .com or .net extension!
A “Zero Trust” policy should be applied.
An extension of any kind can no longer be a guarantee of security and peace of mind on the Internet.
Remember: if your contact is called “EntrepriseO”, she must contact you via an e-mail address such as prénom.nom@entrepriseo.com, or nomduservice@entrepriseo.com, or at the very least, this address must include the company’s name.
Examples: franck.dupont@entrepriseo.com or f.dupont@entrepriseo.com or serviceclient@entrepriseo.com
Also beware of e-mail address terminology that is not what you’re used to, such as f.dupont@entrepriseo.fun
3. Before clicking on a link, hover over it with your mouse or inspect it with your smartphone without clicking on it!
If you inspect a link via your PC or phone, you’ll quickly realize that it’s a malicious address, as it’s far from being similar to a safe URL.
To return to the previous example, we could already see a glimpse of a strange link from the inbox, with the beginning of the URL in http, followed by a foreign organization name.
On the next visual (the one in the middle), there’s also a suspicious address written in small characters with the extension .fun, which doesn’t correspond to the SHEIN.fr brand universe.
On the “Start survey” button, you can preview the link to which you wish to be redirected by hovering over it with your mouse, or by holding down your finger on the button from your cell phone, as in this example.
You can then copy this address and paste it into your search engine, to give you a precise idea of its construction and authenticity.
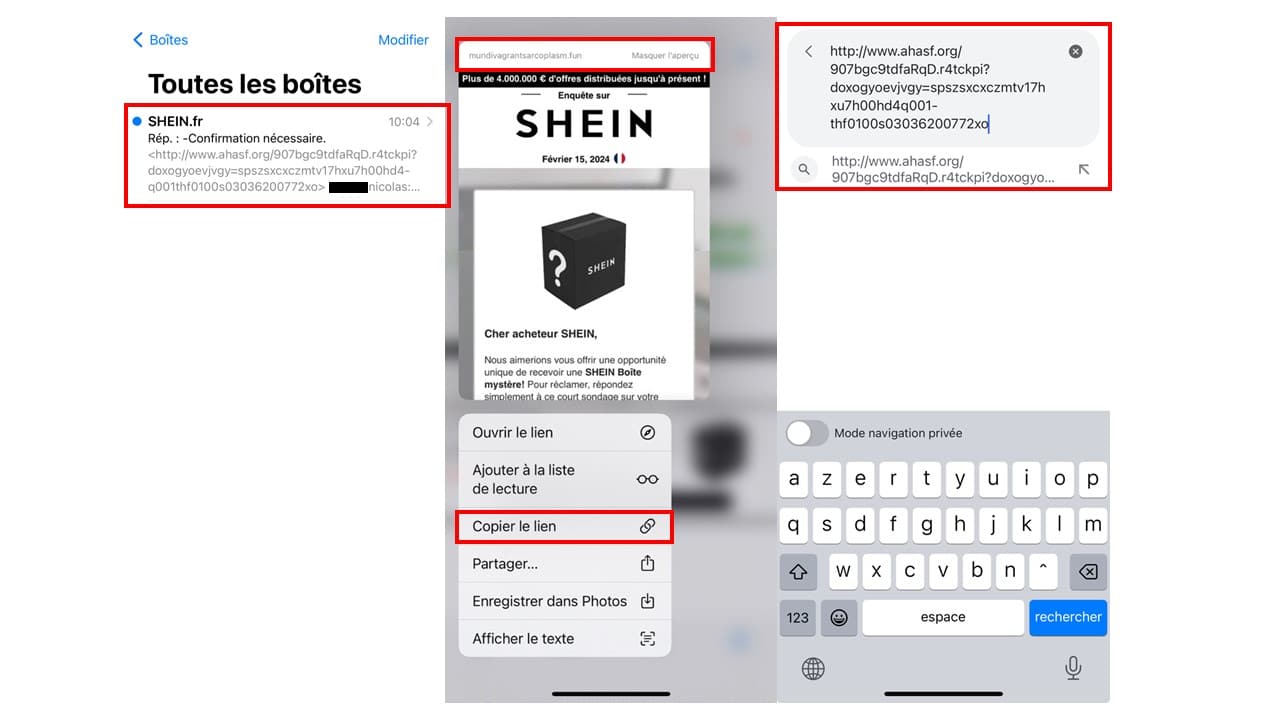
We’d like to point out once again that this link must not be clicked, and so you shouldn’t press “Enter” to obtain a search result, which would take you into the hands of a hacker.
3. Check the site address displayed in your browser.
Through an e-mail falsifying the graphics and structure of letters from your bank, your favorite ready-to-wear website or, more broadly, a trusted third party, you’ll find yourself faced with information that will make you want to click to find out more.
This can be motivated by fear:
– pay your fine within 10 days before it is increased
– regularize your overpayment from the CAF, or FranceTravail (ex pôle-emploi)
– your account has been hacked, change your password immediately
This can be motivated by the lure of winning:
– you’ve been drawn, and you’re the lucky winner of a trip to Bali!
– €150 paid into your Fnac account for the purchase of your favorite games console!
– you’re about to win a whole range of products on Temu for just €1!
This may be motivated by the short deadline for action:
– pay your fine within 48 hours or risk prosecution,
– only a few hours left to win an electric bike by filling in the following questionnaire.
Here you’ll see a number of social engineering techniques that will always drive you to find out more, via a link that will then take you back to an interface that’s almost identical to the site you’re used to visiting.
The aim is always to manipulate you and extract confidential, personal or banking information.
To avoid falling for this trick, there’s a very simple technique that involves checking the link you’re sent:
– or by copying it and pasting it into your web browser (without launching the search!) so that you can see where it really comes from.
– or by using a link checker such as
Urlvoid.com or the one offered by
Google Transparency Report,
– or via the link checker integrated into your antivirus software, such as those offered by Norton SafeWeb and KarsperskyThreat Intelligence Portal.
– or by downloading a dedicated API.
Using a VPN (Virtual Private Network) also gives you an extra level of security when using your electronic devices or the Internet.
3.1. Vérifiez que vous êtes sur un site web sécurisé dont l’URL débute par https (et non pas par http)
Without drowning you in technicalities, a site beginning with https has an additional security feature that encrypts your data, and secures the data exchanged between your browser and the site’s server. In short, your connection is secure with a site whose URL begins with https, whereas it is not with a site whose URL begins with http.
Hackers also know how to reproduce https links!
This technique alone is not enough: you need to supplement it with other verification elements from this list to be fully sure of a link’s authenticity.
3.2. Entrez manuellement l’adresse de votre site dans votre navigateur
The safest way to make sure you’re visiting the right website (with the right link) is to type the name of the site you want to be redirected to into your browser’s search bar.
By proceeding in this way, you’ll eliminate a high probability of clicking on a malicious link, and falling into a social engineering trap.
Example: when opening an e-mail, you might spontaneously click on the wrong e-mail address to go to Amazon, by clicking on the first URL in our example below, rather than on the second, which is the right one:
1- https://www.αmαzon.fr/
2- https://www.amazon.fr/
Be very careful when reading, on the internet, the devil really is in the detail!
4. Check for language and spelling mistakes
Phishing messages can be well-written, and it’s sometimes even too difficult to tell the real from the fake by simply reading them. But these e-mails are often riddled with spelling, syntax and expression errors.
Emojis, for example, are not customary in service companies, energy suppliers and the administration, especially for e-mail and SMS.
If you notice that an e-mail contains too many spelling mistakes and that the language is not what you’re familiar with, then there’s a good chance that it hasn’t come from a reliable source.
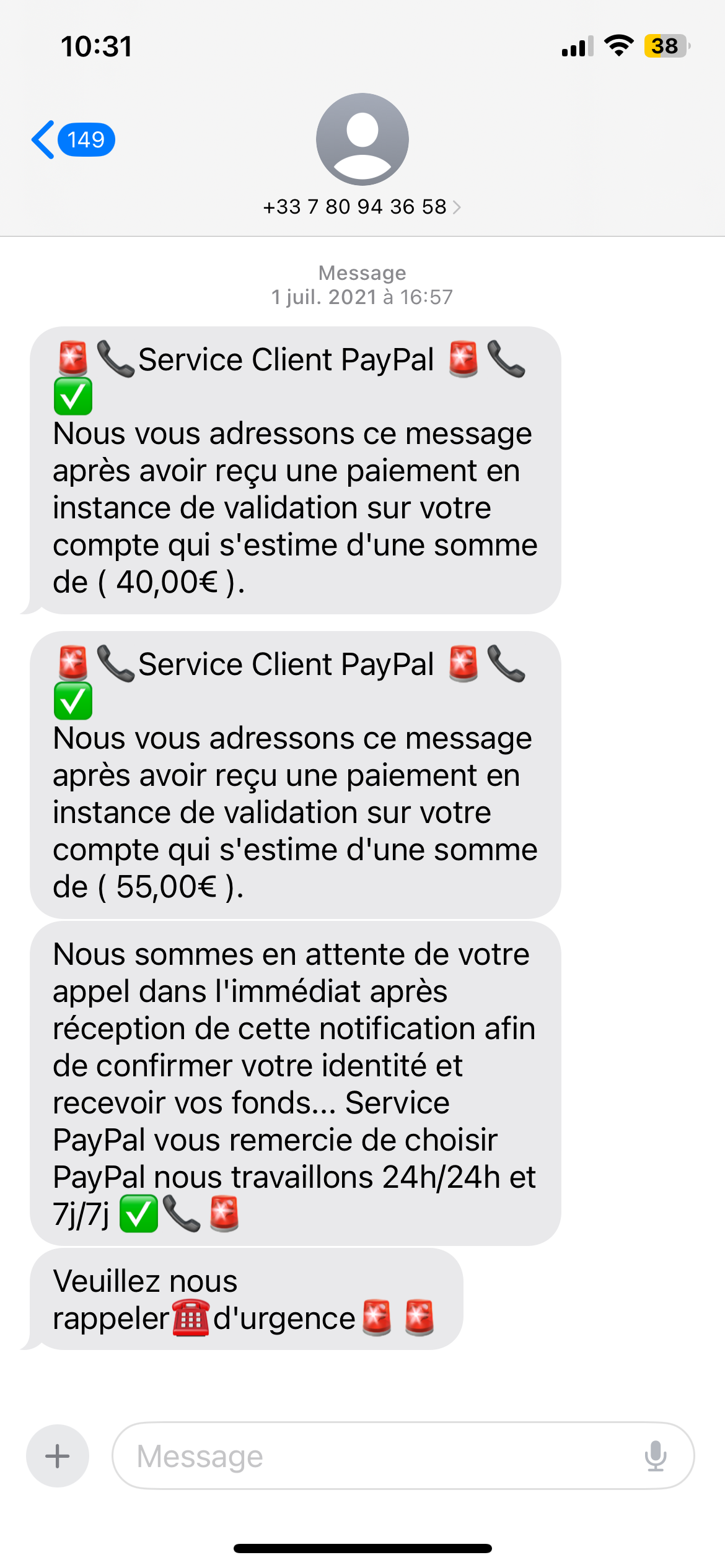
5. If in doubt, contact the relevant organization yourself
There are several types of phishing, of which e-mail is the most widely used by hackers.
But you also need to be aware of other malicious practices such as phishing by sms (called Smishing) or phishing by phone (called Vishing).
As with e-mail phishing, these techniques involve impersonating a trusted third party to trick you into carrying out a transaction.
With SMS, the principle is the same as with e-mail phishing, but on cell phones. For example, you’ll be sent a message inviting you to click on a link, or you’ll be warned that you’ll soon be contacted by phone to tell you about an extraordinary offer, or to tell you that there’s a threat hanging over you and that you can eradicate it with the help of their service.
The aim is the same, but the process is different.
To be sure that an e-mail, SMS or call is genuine, contact the organization that contacted you via your usual e-mail or telephone contacts. They will then be able to guarantee that the message you have received is genuine or not.
6. Use different, complex passwords for each site and application.
It’s not uncommon for users to get lost between their many passwords. There are those used to log on to your computer, your e-mail address, your Ameli.fr account, your professional logins, etc…
So why make it complicated when you can make it simple, and have the same password for all these tools and devices?!
To fight cybercrime, you need to have several passwords, and even a different one for each device and each use.
But don’t make your passwords too simple either: azerty, 0000, 0123, your year of birth or your city followed by your year of birth.
Because these passwords are very easy for cyber hackers to find, you need strong passwords that respect at least 10 characters, a lowercase letter, an uppercase letter, a number and a specific character.
But if you want to find a strong password on your own, you can also write a whole sentence, or even an SMS message from the 90s, when characters were limited and SMS messages were still paid for!
Example sentence / password: En1998,Zizouétaitleroi!
Example of SMS 90″/ password: iRGHT2pK2lé (Yesterday, I bought two packs of milk)
To go one step further, you can generate strong passwords via electronic devices such as smartphones and search engines, or with online strong password generators such as Avast Random Password Generator, or via software such as KeePass, which lets you store all your passwords and generate them in a single application.
6.1 Separate your personal and professional uses.
Don’t use the same passwords at home and in your organization.
The link between your personal and professional activity is very easy to make for a hacker, and for anyone with professional social networks. But if you use the same passwords in both worlds, you’ll be vulnerable on both sides if you get hacked even once on one of your personal or professional accounts.
7. Check the date and time you last logged on to your account.
Some sites and applications can identify the dates, places and times of the last connections made with your user account. This is the case for your Google account, for example. By keeping track of your last logins, you’ll quickly be able to see if there’s been any unusual connection to your account.
In some cases, you can activate an e-mail alert for each connection made to your user accounts, for even more advanced monitoring.
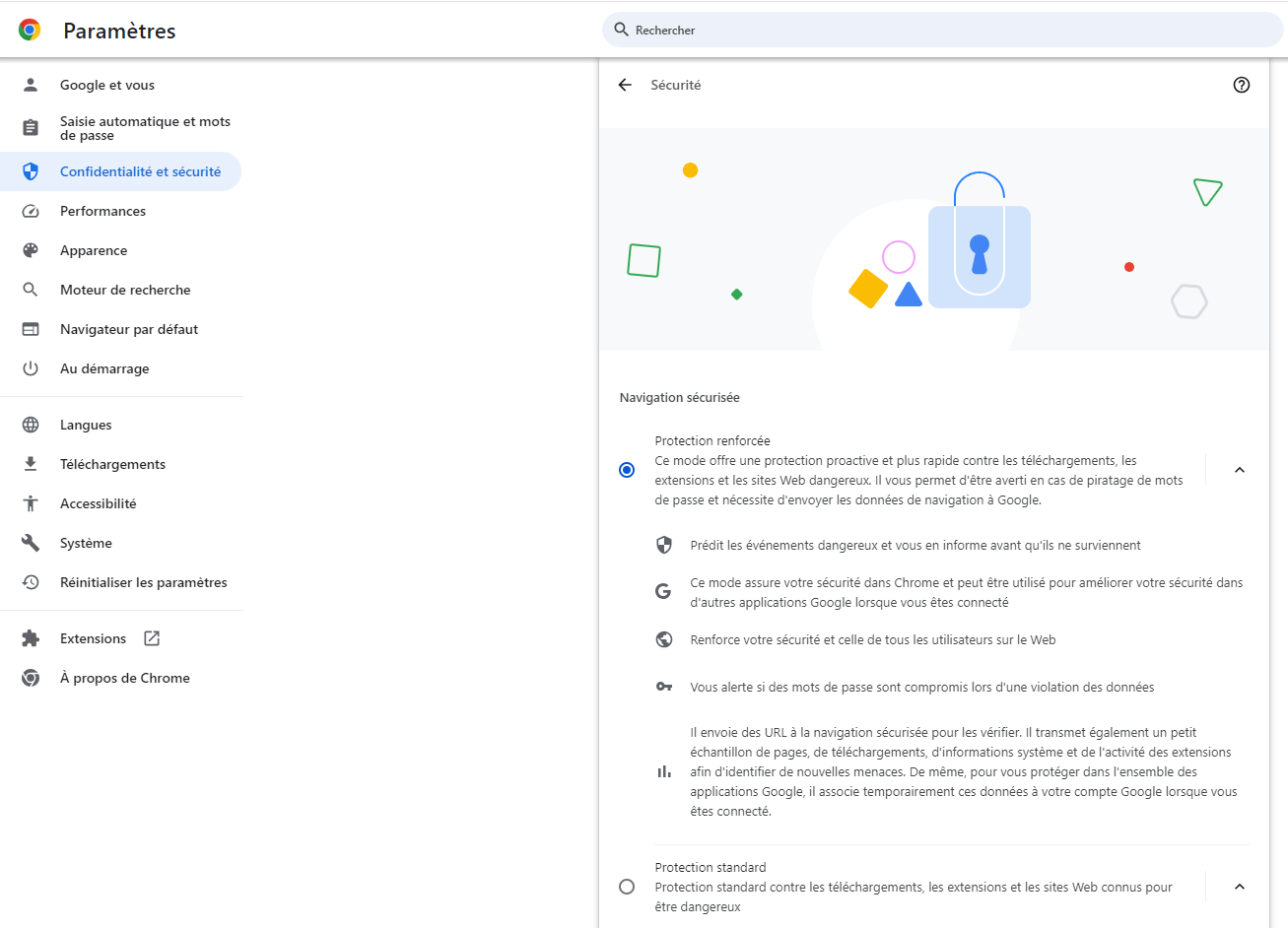
8. Use your browser’s phishing filter
Whether you use Google Chrome, Mozilla Firefox or Internet Explorer, you can enhance the security of your web browsing. In your browser settings, you’ll find a section dedicated to your security settings, to filter out unsecured links, and therefore phishings.
Spontaneously, we don’t necessarily think about protecting ourselves with the tools we have at our disposal, thinking that these tools are already safe and guarantee a level of protection commensurate with the trust we place in them, and yet, without our knowing it, our own tools can protect us a little better (and for free).
9. Install anti-spam software
Phishing e-mails can be identified by antispam software, and filed directly in your junk mail folder so as not to expose you. By doing this, anti-spam software can prevent you from opening malicious links, being exposed to viruses or even inadvertently downloading malware.
10. Download your applications only from official sites
Entering a malicious site actually exposes you to intrusions into your devices or applications. Avoid malware-infected downloads and malicious spamming by not exposing yourself to unsecured or unofficial platforms.
11. Avoid public or unknown Wi-Fi networks
In both professional and personal contexts, connecting to a public Wi-Fi network exposes you to considerable risk of intrusion into your computer systems and connected devices.
By public Wi-Fi, we mean a Wi-Fi network that is open to everyone, and therefore to potential criminals. When you connect to a public Wi-Fi network, there’s a good chance that you’ll have to enter certain information and click on links to connect. This is the gateway to phishing, but not the only one.
For example, some hackers may embed malware or spyware in these links, which are downloaded directly to your device. If you log on to your bank, or use your social networks, these accesses could then be corrupted and stored in software driven by a malicious third party.
Opt for your own 4G or 5G mobile network whenever possible, rather than connecting to a public, open network!
12. Information, awareness-raising and training to deal with online risks
If you’re already aware of the risks of the Internet, you’re less likely to fall into common traps such as phishing. On the other hand, if you’ve never heard of these fraudulent practices, then you’re very likely to fall for what’s known as social engineering. Hackers go to great lengths to trick you into revealing personal information such as login details, passwords, identity documents and bank details.
Whether at home or at work, it’s becoming increasingly important to know how to secure your devices and your online experience.
To raise your awareness of online threats and best practices, ask your employer for information on this subject. It’s likely that a DSI (Direction des Systèmes Informatisés) department will have documentation to share with you, or can organize in-house workshops to train you in the fundamentals of digital security.
Alternatively, you can always request training to benefit from the expertise of an entity outside your organization.
Numeryx offers a range of solutions, including awareness campaigns and even training, for companies wishing to make their employees the first line of defence against external threats, rather than the gateway to them.
You can find ourcustomer references andcybersecurity training courses on our website and that of our training organization Numeryx Université.
13. Visit the Cybermalveillance.gouv.fr platform
The Cybermalveillance.gouv.fr platform enables all Internet users to obtain ongoing information on good digital security practices for the general public and businesses, via a range of communication channels including social networks.
As a service provider listed by Cybermalveillance.gouv.fr, Numeryx provides information and advice on how to protect yourself and (re)act against all types of online attacks and scams.




