There is such a thing as a hacker who means well! He’s known as the ethical hacker, or the white hat hacker, and more commonly as the White Hat Hacker.
Ethical hacker: definition
It’s about a computer security expert who uses his skills for honest and ethical purposes, and who, somewhat caricaturistically, is on the side of justice.
This hacker profile can be recruited internally, or can be commissioned by companies to test the security of their network, web applications or any connected hardware, more widely known as IoT (Internet of Things).
The role of an ethical hacker is to find vulnerabilities in an organization’s computer systems that a malicious hacker called a Black Hat Hacker, or an opposing malicious hacker organization, could exploit to compromise an organization’s information system.
The white hat hacker uses his knowledge to compromise the organization’s systems himself, just as a black hat hacker would have done, with the difference that the ethical hacker needs the organization’s authorization to carry out these penetration tests.
This contract between the organization and the ethical hacker is called the intrusion mandate. It is only with this mandate that the ethical hacker is authorized to carry out penetration tests. Without this mandate, every hacker is considered a cyber-attacker, whose aim is to harm the organization.
The ethical dimension lies in the fact that, instead of using his discoveries for his own benefit and/or malicious purposes, the white hat hacker will propose to his employer or the organization that commissioned him, a plan of action to remedy the flaws detected.
Ethical hackers can be either internal or external to an organization, but will be mandated in both cases.
The internal ethical hacker:
He may be required to have intimate knowledge of just one type of software or digital asset to specialize in a specific type of intrusion, or just one type of device or network to hack.
The external ethical hacker:
This is a major difference from an in-house hacker, since he knows little or nothing about the organization, and can therefore put himself 100% in the shoes of a Black Hat Hacker, as in a real situation.
What are the skills of an ethical hacker?
The ethical hacker is a specialist in simulated offensive cybersecurity services.
- He must master operating systems (Windows and Linux),
- It must include wired and wireless networks, and their infrastructures,
- It must include firewalls and file systems,
- He needs to know how file permissions work,
- He must have solid coding skills,
- He must be familiar with servers, workstations and IT in general,
- He must be familiar with the various automatic and manual attack methods.
- He must be familiar with attack tools.
Knowing how to attack an information system is a prerequisite for this type of job. It is often said that, to protect yourself from a malicious hacker, you have to try to understand him by putting yourself in his shoes, to better simulate the types of attack he might think of. To best put yourself in his position, you need to be able to think in his place, and carry out attacks on the system to be defended with the same know-how, the same knowledge of tools and attack methods.
As hacking techniques evolve, the ethical hacker must be able to update his or her knowledge and skills on these new threats and practices. It’s essential that they keep a constant watch on the cyberthreats that are spreading on the net, all over the world. He or she must be able to provide a fresh perspective on the different types of online intrusion and aggression, so as to be able to defend against them in the best possible way.
It must be ethical in its strictest and most precise definition.
If you scour the net, you’ll find a few stories of Black Hat turned White Hat, when this new benevolent role emerged among hackers. Although technical skills may be similar, a background as a cybercriminal is eliminatory to becoming an ethical hacker.
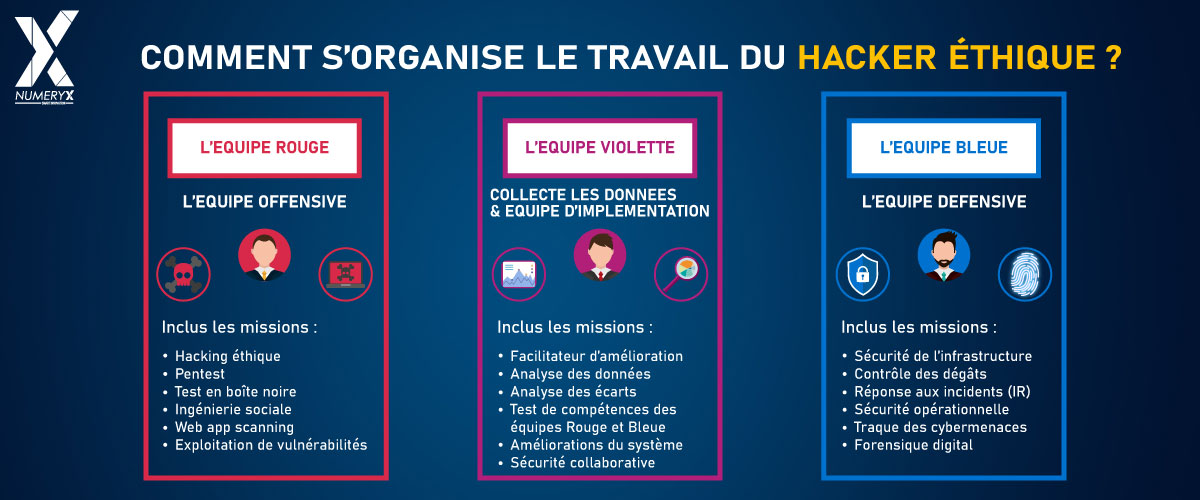
Among these ethical hackers, there are different roles, and even different teams:
The Red Team, a team of penetration testers
The red team provides offensive security services by imitating the role of a cyber attacker.
It is common for the red team to be external to the organization, which commissions them to imitate an attack from outside, without any prior knowledge of the security system in place.
The types of attack that can be implemented by the red team are numerous.
They involve exploiting “standard” vulnerabilities, as well as more complex attacks such as social engineering, or psychological hacking.
The Blue Team, a defensive improvement team
The blue team therefore provides defensive security services. Unlike the red team, the blue team is already aware of the organization’s defense system. It continuously analyzes unusual activities in the computerized system, using security auditing, log analysis or risk scenarios.
It’s a job that involves an enormous amount of attention to detail, so as not to miss an unusual or foreign piece of code, for example.
The Purple Team, the union of Red Team and Blue Team
Combining red and blue, the purple team identifies the teams that provide part of each type of security service, red and blue. In reality, this is a joint effort by the two teams, and a cooperative effort to strengthen knowledge of cyber attacks on the one hand, and cyber defense on the other.
How to become an ethical hacker
Historically, the ethical hacker was a self-taught individual who acted alone and without any particular training. Yesterday’s ethical hacker was more of a Grey Hat Hacker, acting for the good of one or more organizations by hacking into their systems without prior authorization or intrusion warrant, but informing the organization concerned of existing security flaws in their information system or network.
In the United States, it is common practice for self-taught hackers who claim to be White Hat to be hired following bug fixes via bug bounty platforms by companies who have fallen victim to these “bugs”, which present security flaws in their computerized systems. This is the case, for example, for companies such as Facebook and Google.
In France, most ethical hackers are already experts in information systems or network security. They are very often trained in cybersecurity, with cybercrime as a second step. In the vast majority of cases, therefore, this is a change of position rather than a change of function.
The script kiddie, or the definition of an amateur hacker

Not just anyone can be an ethical hacker! Script kiddie, also known as lamer (meaning “weak” or “lame” in English), is a pejorative term used to describe computer neophytes who try to infiltrate systems by any means necessary, without any computer security skills.
The script kiddie is the type of profile that uses simple programs, even those already designed by other experienced hackers, but which they don’t understand, and claims responsibility for large-scale attacks to give themselves legitimacy.
Despite their low level of skill, script kiddies can represent a real threat to system security. On the one hand, because script kiddies are very numerous, and on the other, because they are often so persistent in their actions that they may spend several days attempting several different attacks.
However, with their lack of knowledge and skills, script kiddies take few precautions when acting. They make fairly basic mistakes that make them easy to identify, and therefore easy to hack.
Today, the starting point for becoming an ethical hacker is above all training, and can be reinforced by obtaining one or more certifications.
What training do you need to become an ethical hacker?
What training do you need to become an ethical hacker?
To become an ethical hacker, you logically need a good level of computer science, as well as a specialization in cybersecurity.
To achieve this, you can train at Bac +3 level, or continue to Bac +5 and beyond.

This type of training can be taken at university, engineering school or specialized school, with a focus on cybersecurity.
After that, it’s entirely possible to become an independent ethical hacker, or to join an organization.
What certifications does it take to become an Ethical Hacker?
Indeed, there are specific certifications for ethical hacking. Two of the most famous worldwide are the CEH – Certified Ethical Hacker certification and the OSCP – Offensive Security Certified Professional certification.
- Certified Ethical Hacker (CEH) certification
This CEH certification has recently been revised to offer a complete and updated 11th version.
Recognized worldwide by security professionals and compliant with the ANSI 17024 standard, CEH certification is a real added value to your CV and career path in the world of cybersecurity, penetration testing and, more specifically, ethical hacking.
The course culminates in a 4-hour multiple-choice exam.
- Offensive Security Certified Professional (OSCP) certification
OSCP certification is designed to demonstrate the skills and knowledge needed to be a penetration tester.
If you want to build your career in cybersecurity, this certification is for you.
If you want to learn more about defensive and offensive techniques in penetration testing, then you should consider certification to become an Offensive Security Certified Professional (OSCP).
Unlike CEH certification, OSCP is not a MCQ-type exam. The aim here is to put your knowledge into practice with a remote LAB, which will assess your technical skills as well as the quality of your reporting.
Interested in training or certification in cybersecurity?
Visit the ” Cybersecurity ” section of Numeryx Université to discover 13 Cybersecurity training courses, either classroom-based or distance learning.
What are the ethical hacker’s missions?
The ethical hacker bypasses the security rules of the organization that has commissioned him/her. He organizes a computer attack, or a series of attacks, to detect breaches in the organization’s information system, then notifies the organization so that it can remedy them.
In its scope, the ethical hasher will not only perform vulnerability tests (Pentester activity), but will also conduct other work, the main ones being:
Intrusion and regression testing
There are a number of tests to be carried out, including the following non-exhaustive list:
- External network penetration tests,
- Intrusion testing of the internal network,
- Web application penetration testing,
- Mobile application penetration testing,
- Wireless network penetration testing,
- Regression testing,
- Testing of embedded devices,

Identifying security misconfigurations
To reduce the risk of attacks on their networks, companies are required to follow security rules specific to their sector of activity, and to apply them wherever possible.
However, it’s not uncommon for these procedures not to be applied correctly, giving malicious hackers opportunities to spot and exploit security loopholes. In the firing line is the loss of sensitive and/or strategic data through theft, deletion or by making it inaccessible via ransomware, and many other threats besides. Ethical hackers therefore need to check that these security measures are being respected, by taking stock:
- Is there encryption of documents and directories?
- Misconfigured web applications, unsecured devices?
- Is the retention of default identifiers still in place and systematized?
- Is the use of weak passwords persistent?
It may sound basic, but these few points are very common in the corporate world, and constitute a large number of IT security breaches, all as simple to resolve as they are dangerous for an organization.
Setting up vulnerability scans
The first step for the ethical hacker is to map all the company’s networks, with a view to classifying them by importance. This network mapping is a necessity to discover new devices and network interfaces, and to visualize physical and virtual network connectivity.
Network mapping therefore offers complete visibility of a company’s IT infrastructure, to identify which parts of the network need to be secured as a priority, based on the value and volume of information.
Vulnerability scans enable companies to verify the compliance of their networks and security systems. Vulnerability analysis tools will pinpoint security flaws that could be dangerous to systems in the event of an attack.
Preventing exposure of sensitive data
In the event of loss of sensitive or confidential data, companies are exposed to financial penalties for breach of privacy, in addition to the loss of revenue caused by this loss of data, and the other damage it causes (loss of confidence on the part of customers, end-users, shareholders, etc.).
To protect themselves from this potential loss of sensitive data, ethical hackers carry out penetration tests to identify these types of vulnerabilities in the information system, and to document the modus operandi of possible attacks.
Checking for authentication flaws
By compromising the authentication of an organization’s website, attackers can retrieve a wealth of data such as passwords, cookies and user account information. This information can later be used to impersonate employees, or to gain access to more sensitive or even confidential levels of information.
The mission of the ethical hacker in this case is to check the management of authentication systems, and suggest security measures to be implemented to protect the organization.
There are, of course, many other missions for the ethical hacker, such as :
- Evaluations of mainframe systems or applications,
- Evaluation of the application security program,
- Code security review.
You might be wondering how much an ethical hacker is paid for all this good, loyal service?
How much does an ethical hacker earn?
On average, a novice ethical hacker working in France will earn 4,000 euros gross per month, compared with 7,500 euros gross for a senior profile. An increasing number of professionals are also rewarded for solving bugs through bug bounty platforms.
What’s the difference between Black Hat Hackers and White Hat Hackers?
It may be a fine line in technical terms, but it’s a huge one in moral terms!
The white hat hacker, also known as the ethical hacker, is, as his name suggests, on the right side of the fence.
He acts solely with the knowledge of an organization that has commissioned him to test the vulnerability of its computer system, in order to report back and take effective measures to strengthen this computerized system and remedy any flaws that may have been detected.
These penetration tests and methods are not intended to harm the organization, but only to strengthen it.
The Black Hat Hacker doesn’t ask anyone’s permission to break into a computer system. His intention is to harm, destroy or steal data.
Finally, because not everything is black and white, there’s a profile that straddles both worlds, known as the Grey Hat Hacker. Like a black hat, a grey hat hacker can sneak into a system and look for flaws without prior permission, but with the difference that he or she can then pass on the security flaws to the hacked organization (for a fee, or not).




