With the increasing digitization of their activities, companies are increasingly using cloud solutions to store a large part of their business, whether it’s private data, some personal data, and sometimes even inadvertently, sensitive data.
As digital information flows intensify and accumulate day after day, IT resources are increasingly needed to process all these information flows, and this in turn means that networks need to be redesigned to optimize and secure them.
To meet this type of need, companies can:
– leverage an SDN1 software-defined networking platform, and simultaneously,
– reduce the complexity of this solution by using an SD-WAN2 overlay.
SDN (or Software Defined Networking), is a model of network architecture defined and managed on software
SD-WAN (or Software-Defined Wide-Area Network), is literally a software-defined wide-area network, and more precisely, a software technique aimed at making wide-area networks more intelligent and flexible.
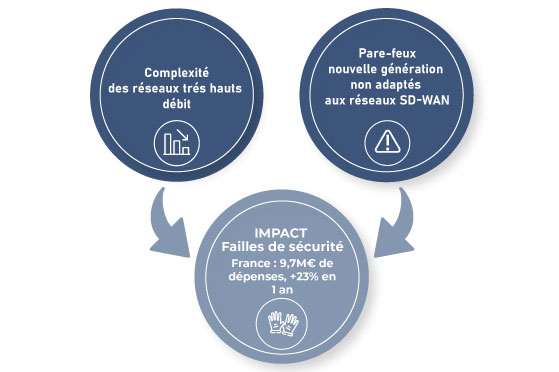
What drives innovation in our Asguard Next-Generation Firewall?
As new networks emerge, so will new network security vulnerabilities.
Introduced in 2018, third-generation SD-WAN IT networks meet the growing needs of businesses, and represent a major evolution in telecoms systems.
It was when we realized that there was no European B2B security solution optimized for SD-WAN networks, and that companies were forced to use security solutions that had become unsuitable, that we launched our project over 3 years ago to develop the first optimized, interoperable European security solution suitable for SD-WAN networks.
The main types of attack on SD-WAN networks
On the global subject of securing SD-WAN networks, it has been identified that attacks on international business groups come from several sources:
- Flooding a network to prevent it from functioning;
- Disruption of connections, preventing access to services ;
- Obstructing access to a service ;
- Sending billions of bytes to an Internet box, for example.
The vast majority of NGFW next-generation antivirus and firewall products secure software-defined networks (SDN). The latter combine the capabilities of traditional firewalls (packet filtering, NAT address translation, URL blocking and VPN) with QoS management functionalities, and features generally absent from firewalls.
These include intrusion prevention, SSL and SSH inspection, deep packet inspection (DPI), reputation-based malware detection and application awareness. Next-generation firewalls are able to detect and block sophisticated attacks such as the aforementioned DoS (Denial of Service) attacks by applying security rules at application, port or communication protocol level.
Today, with the increase in filtering rules, the consumption of IT resources and the complexity of network configuration and management, the number of cyber attacks is increasing on networks and particularly third-generation networks, SD-WAN.
Introduced in 2018, their novelty makes them a perfect playground for hackers, as the NGFW-type security techniques employed to date are not adapted to this technology.
After more than three years of R&D dedicated to securing SD-WAN architecture, we seized the opportunity to include network security services at a high level by developing a next-generation firewall (FWNG) called Asguard.
What is Asguard?
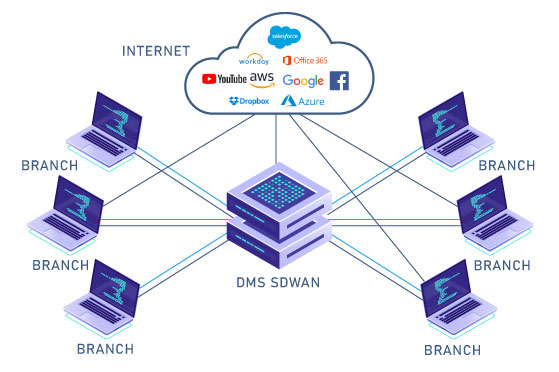
As a next-generation firewall, the Asguard solution will protect your company from the risks of attack, by interposing itself between the customer network and the Internet, whatever the method of access (from the company’s offices, or via a remote client, even a mobile one).
This latest-generation firewall (NGFW) provides optimized, interoperable security for SD-WAN networks.
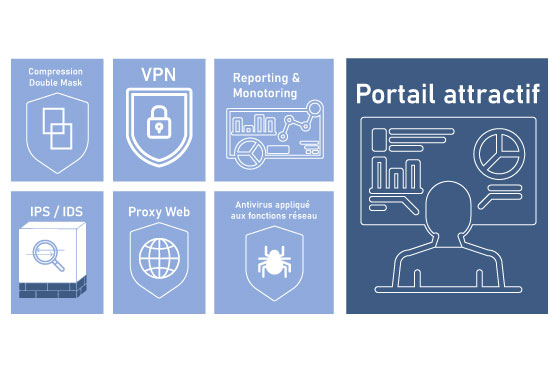
What security features does Asguard’s New Generation Firewall offer?
Thanks to its R&D work over several years, NUMERYX Technologies has been able to develop a lightweight, high-performance security solution, now patented: dual-mask IP filtering. The solution is protected by a patent filed in 2015.
- Level 4 firewall: IP Double Mask filter
The dual-mask IP filter is an innovative IP mapping technique that provides greater flexibility as well as secure and efficient deployment of security policies.The IP filter comprises a first mask, adapted to express a first set of allowed IP addresses, and a second mask adapted to express a second set of IP addresses to be excluded from the first set of allowed IP addresses. This technology enables a clear compression of filtering rules, which can reach over 80%.With this patented technology, we can now generate well-formatted, more compact access control lists at a lower cost to network equipment.
- Virtual Private Network (VPN)
Enables end-to-end encryption of information flows between the customer and his internal or external contact.
VPNs are renowned for their ability to secure connections by encrypting traffic entering and leaving your device, making it more difficult to access your web data. What’s more, even if someone with malicious intent were to get hold of information about you, they couldn’t exploit it because VPN software uses very powerful encryption algorithms. VPNs therefore protect all your personal data (passwords, bank details, websites visited…).
- Intrusion detection and prevention (IPS and IDS)
Allows you to be alerted to a vulnerability or weakness in your system before any intrusion attempt, to identify and locate it, and then automatically organize an outcry against a proven or unproven intrusion or attack.
A key feature of an IPS is that it must be completely stealthy. This means that the probe’s interfaces must not be visible (no IP address, no MAC address) and that the equipment must not behave like a proxy or implement address manipulation mechanisms (such as NAT).
The IPS analyzes all packets in transit, from the network layers down to the application level.
- Asguard is the perfect web proxy:
Based on Squid, it provides caching or pass-through filtering and multi-interface support. It allows multiple users to share an Internet connection over a single connection, and also features a query caching mechanism that allows data to be accessed using local resources instead of the web, thus reducing access time and bandwidth. It also records users’ access to the sites they have visited.
SQUID offers the following services:
- User authentication
- Access filtering
- Query logging
- Proxy cache
- Reverse Proxy
- The transparent proxy
- ClamAV antivirus
Designed for fast file scanning with real-time protection (Linux only), the scan daemon supports on-access scanning, including the ability to block file access until a file is scanned.
It detects over a million viruses, worms and Trojans, including Microsoft Office macro viruses, mobile malware and other threats.
Signed signature databases guarantee that ClamAV will only execute approved signature definitions.
ClamAV scans archives and compressed files, but also protects against archive bombs.Its built-in archive extraction capabilities include Zip, RAR and 7 Zip.
- Reporting & monitoring
Asguard’s reporting solution lets you view network activity and intrusion attempts.
Monitoring gives you real-time access to a complete visualization of your network(s), allowing you to observe its status at any given moment.
- An attractive user portal
The user portal available to each customer enables them to quickly and intuitively consult their network statistics and extract reports.
It enables all functionalities to be controlled from a single, common interface in a uniform way, with the possibility of customizing all parameters without the need for code. The portal is based on Role Based Access technology, which differentiates user roles and privileges.
How does Asguard secure SD-WAN networks?
The technological breakthrough offered by NUMERYX has all the factors needed to succeed in reducing, if not eliminating, the security vulnerabilities of large companies in the long term, as communication networks evolve.
The long-term objective is to create an innovative, next-generation firewall specializing in new technologies and environments (SASE, 5G, SDN, etc.).
Legend: The Secure Access Service Edge (SASE) platform, to which NUMERYX Technologies technology is adapted.
The Asguard solution can also be adapted to other network technologies, such as 5G radio networks or SDN (Metro Ethernet) networks. Indeed, 5G networks bring the concept of “network slice” or “Virtual Network Embedding” to deliver differentiated services to its users. Each network slice provides an end-to-end service, made up of different network components and virtual systems based on a shared infrastructure.
Qualifications & Partnerships
We’ve been with you from the very start of the Asguard adventure and the world of cybersecurity, from the filing of our patents to R&D, from the support of our work to the development of our company, and we can’t fail to mention the major partners and players in our success:
INRIA:
NUMERYX Technologies’ work focuses in particular on the development of a distributed filtering technology in these slices to better distribute filtering rules across switches and network functions. In partnership with INRIA, the company has developed algorithms to distribute these rules across the various devices, so as to balance the load on the tables, enable upstream filtering of malicious packets, and make it possible to share these tables for slices created by service providers. The proposed technique is also applicable in environments such as the cloud and the datacenter.
INPI :
A national patent was filed in 2015: Bouhoula, A., and Ben, N.N. (2015). “Filtre Ip a Double Masques,” FR3011705 (A1). The innovative Asguard project is based on this patented technology.
ANSSI:
Convinced of the commercial impact of such certification, NUMERYX is aiming for First Level Security Certification (CSPN), set up by ANSSI.
This certification assesses the product’s resistance to moderate attacks.
At a later stage, the company is considering qualification with a security visa, enabling it to access French and European regulated markets.
Certification and qualification will give the company a competitive edge in the French and international cybersecurity markets.
The Systematic competitiveness cluster:
Who approved Asguard as an innovative project?
French Tech Paris-Saclay:
Our partner and supporter in the development of NUMERYX since its inception and incubation at SQYcub.

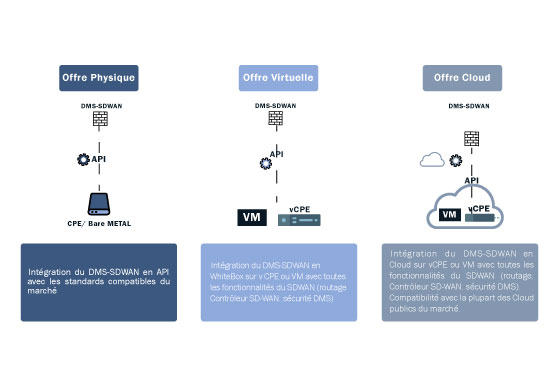
NUMERYX currently offers three solutions to address different customer contexts:
- Offer 1: Integration of Asguard on physical equipment (CPE9) ;
- Offer 2: White-box integration of Asguard on virtual hardware (virtual machine, vCPE10 on classic hosting);
- Offer 3: Integration of Asguard in the cloud on virtual devices (virtual machine, vCPE hosted in the cloud). This offer applies to both private and public clouds.
Value proposition
Asguard offers a differentiating value proposition based on a solution that is both :
– Secure, perfectly adapted to the specific requirements of SD-WAN networks
– Compatible with industry standards
– Optimized thanks to high compression ratio
– And interoperable thanks to solution APIsation
The APIization of the solution makes it universal, which is a major advantage compared to other players, who provide specific, locked-in solutions for a precise network technology.
Thanks to the development of an API, the solution can be integrated by all editors and integrators on the market.




